Hello Cloud Marathoners,
The following post is going to be covered in the Azure Spring Clean 2022 event’s website too. Thus, you might be wondering what the Azure Spring Clean is?
Azure Spring Clean 2022 Overview
The Azure Spring Clean is a community-driven event focused on Azure management topics and gradually publishes content from March 14-18, 2022.
I would like sincerely Thank – Joe Carlyle and Thomas Thornton for putting time and effort in organizing this event. From a #cloudmarathoner ’s perspective it’s been enjoyable to contribute and be a part of this event. This topic specifically outlines how to understand the pros and cons of your initial Azure AD settings that will be aligned with your project’s expectations.

WHY azure ad security defaults are important?
Indeed, this is a very legit question and I would like to address it with the following quote from Alex Weinert:
…our telemetry tells us that more than 99.9% of organization account compromise could be stopped by simply using MFA, and that disabling legacy authentication correlates to a 67% reduction in compromise risk (and completely stops password spray attacks, 100% of which come in via legacy authentication)…
Alex Weinert – Director of Identity Security at Microsoft
The main purpose behind these default settings is to make sure that all organizations using Azure AD have a basic level of security, and it is enabled at no extra cost according to Microsoft.

Azure AD security defaults are something you need to enable at the tenant level. Once you do this, the rules will apply to all users in your tenant without any exceptions.
If you are looking for enforce rules more selectively ( or exclude some users ) then security defaults won’t be a fit solution for you. For this scenario, you would need to look at getting some P1 or P2 licenses and use the conditional access instead.
How can I set up my Azure AD Security Defaults?
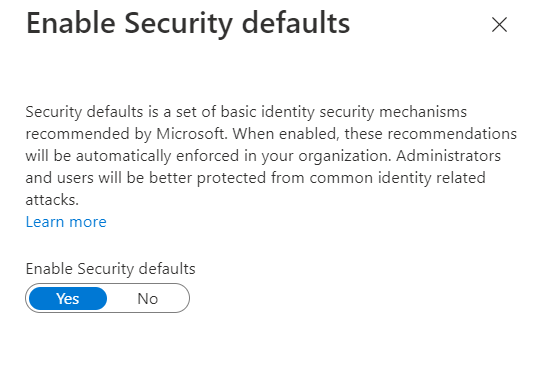
The Microsoft Azure AD team did a fantastic job by simplifying this option. You need to navigate int0 Azure AD -> Properties -> and click on link Manage Security defaults.
You will end-up with the following window on the right panel of Azure portal:
What is baked inside the security defaults in azure ad?
There are a number of things baked into the “Security Defaults” by Azure AD team. You could read about an official and detailed description here – Security defaults in Azure AD.
One of the BIG incentives for the security defaults is that it brings Multi-Factor Authentication (MFA) to your users for #free. Of course, there are some limitations around this which I will cover later on, but this option does allow you to get an MFA with no additional cost.
Previously, you would have to have either Azure AD P1 licenses, or pay per use for MFA functionality. Thus, this is a big game changer benefit that you are getting for free in your tenant and will bring a significant extra level of security. And this defaults includes both Azure and Office 365 services.
Along with MFA, security defaults are enforcing several policies that make your tenant more secure:
- Requiring all users to sign up for MFA (for free)
- Requiring those in Azure administrator roles to perform MFA
- Blocking legacy authentication protocols – this includes clients that don’t use modern authentication and so don’t support MFA, and older mail protocols like IMAP, SMTP and POP3
- Requiring MFA authentication when undertaking privileged actions using the Azure portal, PowerShell or CLI
Will Security Defaults replace my Azure AD licenses ?
In short, the answer is No. Your Azure AD licenses provide more security protection services than what you get from “Security Defaults”.
Think of a “Security Defaults” as a security design approach for users on a free Azure AD tier. Because, if you are already using P1 or P2 licenses you would want to look at using conditional access to perform this (and more) rather than security defaults.

What you need to know before deploying the Security Defaults?
Based on Microsoft security guidelines, every organization should have at least two emergency access accounts configured. These accounts are intended for use when your regular administrator account’s can not be used. A typical example is: when person with the most recent Global Admin access has left your company.
What are the emergency access accounts ?
Well, following three criteria defines it pretty well:
- Aren’t used on a daily basis
- Are protected with a long complex password
- Has an assigned Global Administrator rights in Azure AD

These emergency access accounts and credentials are very sensitive and should be stored in a secure location like a fireproof safe. And only authorized people in your organization should have access to these accounts.
You are also encouraged to disable password expiration to for these accounts using Azure AD PowerShell.
Check out this Microsoft article – Manage emergency access accounts in Azure AD, as it provides more detailed information about emergency access accounts.
What to do when switching from Security Defaults to azure ad Conditional Access Policies?
In order to provide more productivity and better security to your users, you could replicate the policies created by Azure AD Security Defaults. First, your customer’s tenant must be licensed with Azure AD Premium P2. However, the majority of policies can also be accomplished using the Azure AD Premium P1 license.
Check out the following Microsoft documented guides on how you can use Conditional Access to configure equivalent policies to the once that get set by the security defaults:
- Require MFA for administrators
- Require MFA for Azure management
- Block legacy authentication
- Require MFA for all users
- Require Azure AD MFA registration
All these policies could be implemented with Premium P1 license, except the last one. The last policy requires Azure AD Identity Protection feature of the Azure AD and could be provided via Premium P2 license.
Summary
Thank you so much for reading this post and learning about the Azure AD Security defaults. I tried my best to provide my perspective on this important topic while using availiable Microsoft docs and resources.
Please, keep up the good work by securing your and customer’s cloud environments!