Hi Cloud Marathoner friends,
A few days ago, I got the following error when attempting to run a Git command:

Problem
“fatal: unable to access ‘https://github.com/ElYusubov/Learn-Bicep.git/‘: SSL certificate problem: unable to get local issuer certificate”
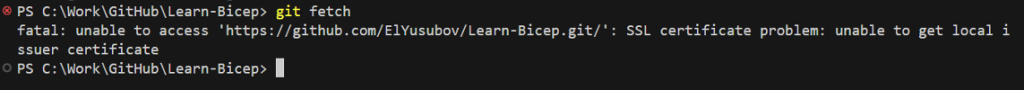
This issue originated from the fact that git by default uses the “Linux” crypto backend.
However, there is a simple solution, from the beginning of version Git on Windows 2.14, you can configure Git to use SChannel. This is a built-in Windows networking layer as the crypto backend. In other words, the Windows networking layer will be used with the Windows certificate storage mechanism and you are not required to configure the curl CA storage mechanism.
If you would like to dig into more technical details, then here is the full article on this topic: https://msdn.microsoft.com/en-us/library/windows/desktop/aa380123(v=vs.85).aspx
Solution
Fortunately, you don’t have to change anything in your Windows environment, just run the following Git command: “git config –global http.sslbackend schannel”.
Let me know if that helped with your problem and keep me in the loop if you had a similar problem.


